Logi VPN
Spis treści:
Logi błędów
PPTP
IPsec
SSL VPN
OpenVPN
Zapoznaj się z przykładem Jak zapisać SysLog.
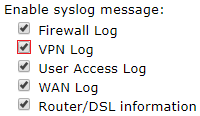
Przejdź do zakładki System Maintenance >> SysLog/MailAlert, aby włączyć logi VPN.
==> dane wysyłane przez router Vigor
<== dane odbierane przez router Vigor
Logi błędów
[PPTP/L2TP/SSL VPN] Problemy z przydzieleniem IP
Vigor nie ma wolnych adresów IP do przydzielenia
– [Local][x:xxx][@x.x.x.x] IPCP NAK:, assign ip or set route error
[OpenVPN] Problemy z przydzieleniem IP
Vigor nie ma wolnych adresów IP do przydzielenia
– OpenVPN (VPN-x, x.x.x.x) AUTH_FAILED,DHCP assign IP error.
[PPTP/OpenVPN] Brak użytkownika “xxx”
– Incoming Call Failed : No Such Entry for xxx
[PPTP/L2TP/SSL VPN] Błędna nazwa użytkownika lub hasło
Uwierzytelnianie PAP:
– (VPN-x, xxx) ==> Protocol:PAP(c023) Authenticate-Nak
Uwierzytelnianie CHAP:
– (VPN-x, xxx) ==> Protocol:CHAP(c223) Failure Identifier
– CHAP Login Failed ()
[PPTP/L2TP] Niezgodność ustawień protokołu uwierzytelniania
Np. klient VPN próbuje PAP a w VPN and Remote Access >> PPP General Setup wymuszony Dial-In PPP Authentication “MS-CHAP Only”:
-Configuration NAK from remote dial-in; peer want PAP, but we support CHAPv2 Only…NAK
[PPTP] Niezgodność ustawień MPPE
Np. klient VPN próbuje PPTP bez szyfrowania MPPE a w VPN and Remote Access >> PPP General Setup wymuszone Dial-In PPP Encryption(MPPE) “Require MPPE” lub “Maximum MPPE”:
– VPN_MPPE_REQUIRED but client reject PPP_CCP_PROTOCOL…shutdown interface
[IPsec] Nieprawidłowy klucz IKE
– [IPSEC/IKE][Local][x:xxx][@x.x.x.x] smalformed payload: probable authentication (preshared secret) failure
[IPsec] Niezgodność ustawień algorytmów pierwszej fazy IKE
Klient VPN próbuje użyć zestawu algorytmów (szyfrowanie, funkcja hash, grupa Diffiego-Hellmana) nie wspieranych przez router Vigor w VPN and Remote Access >> IPsec General Setup:
– [IPSEC/IKE][Local][x:xxx][@x.x.x.x] state transition fail: STATE_MAIN_R0
[IPsec] Niezgodność ustawień algorytmów drugiej fazy IKE lub niezgodność ID np. podsieci
Klient VPN próbuje użyć zestawu algorytmów (szyfrowanie, funkcja hash, grupa Diffiego-Hellmana) nie wspieranych przez router Vigor w VPN and Remote Access >> IPsec General Setup lub w profilu VPN.
Również przy niezgodnej adresacji podsieci w VPN LAN-LAN.
– [IPSEC/IKE][Local][x:xxx][@x.x.x.x] state transition fail: STATE_QUICK_R0
[OpenVPN] Brak wymaganych certyfikatów
Klient nie posiada wszystkich certyfikatów a w VPN and Remote Access >> OpenVPN włączona jest opcja “Certificate Authentication”:
– OpenVPN (VPN-x, x.x.x.x) SSL handshake failed
[OpenVPN] Niezgodność certyfikatów
Certyfikaty skonfigurowane w kliencie nie pasują do certyfikatów w routerze:
– OpenVPN (VPN-x) Negotiation timeout
[OpenVPN] Niezgodność ustawień algorytmów
Klient VPN próbuje użyć zestawu algorytmów (szyfrowanie, funkcja hash) nie wspieranych przez router Vigor w VPN and Remote Access >> OpenVPN:
– OpenVPN (VPN-x, x.x.x.x) Remote cipher or auth not matched so fail
– OpenVPN (VPN-x, x.x.x.x) AUTH_FAILED,cipher not matched.
[OpenVPN] Błędna nazwa użytkownika lub hasło
– OpenVPN (VPN-x, x.x.x.x) AUTH_FAILED
PPTP
Przykładowe logi z serwera VPN (Vigor2926) dla prawidłowego połączenia:
– PPTP accept client from 2.2.2.2:6342 …
– PPP Start ()
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfReq Identifier:0x00 Authentication Type: CHAP 81 Magic Number: 0x1 ##
– PPTP (VPN-0) <== Protocol:LCP(c021) ConfReq Identifier:0x00 MRU: 1400 Magic Number: 0x773451 Protocol Field Compression Address/Control Field Compression MRRU: 1614 Endpoint Discriminator Locally Assigned Address: cc f9 d6 25 6e 8e 4c c5 a2 81 b4 45 94 ff cf…..
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfRej Identifier:0x00 Protocol Field Compression Address/Control Field Compression ##
– PPTP (VPN-0) <== Protocol:LCP(c021) ConfReq Identifier:0x01 MRU: 1400 Magic Number: 0x773451 MRRU: 1614 Endpoint Discriminator Locally Assigned Address: cc f9 d6 25 6e 8e 4c c5 a2 81 b4 45 94 ff cf 5e 00 00 00 11 ##
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfNak Identifier:0x01 MRU: 1442 ##
– PPTP (VPN-0) <== Protocol:LCP(c021) ConfReq Identifier:0x02 MRU: 1400 Magic Number: 0x773451 MRRU: 1614 Endpoint Discriminator Locally Assigned Address: cc f9 d6 25 6e 8e 4c c5 a2 81 b4 45 94 ff cf 5e 00 00 00 11 ##
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfNak Identifier:0x02 MRU: 1442 ##
– PPTP (VPN-0) <== Protocol:LCP(c021) ConfReq Identifier:0x03 MRU: 1442 Magic Number: 0x773451 MRRU: 1614 Endpoint Discriminator Locally Assigned Address: cc f9 d6 25 6e 8e 4c c5 a2 81 b4 45 94 ff cf 5e 00 00 00 11 ##
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfAck Identifier:0x03 MRU: 1442 Magic Number: 0x773451 MRRU: 1614 Endpoint Discriminator Locally Assigned Address: cc f9 d6 25 6e 8e 4c c5 a2 81 b4 45 94 ff cf 5e 00 00 00 11 ##
– PPTP (VPN-0) ==> Protocol:LCP(c021) ConfReq Identifier:0x01 Authentication Type: CHAP 81 Magic Number: 0x1 ##
– PPTP (VPN-0) <== Protocol:LCP(c021) ConfAck Identifier:0x01 Authentication Type: CHAP 81 Magic Number: 0x1 ##
– PPTP (VPN-0) ==> Protocol:CHAP(c223) Challenge Identifier:0x01 10 5d 19 49 15 7d 09 89 05 9d 39 89 35 fd 29 c9 25 44 72 61 79 54 65 6b ##
– PPTP (VPN-0) <== Protocol:CHAP(c223) Response Identifier:0x01 31 e6 b6 b2 74 d9 e1 66 7f e3 03 49 0d 77 44 ea 30 00 00 00 00 00 00 00 00 f5 cf bf bd 30 f7 85 e1 af 6b bf 2c 4d 75 ea 5c 78 ab 4e 15 01 e7 01 7e 00 74 65 73 74 ##
– PPTP (VPN-0, test) ==> Protocol:CHAP(c223) Success Identifier:0x01 S=EFC71C1217A25AE46E67A54C5AF44F988672052F M=Welcome to Vigor2926 Series. ##
– PPTP (VPN-0, test) ==> Protocol:IPCP(8021) ConfReq Identifier:0x00 Compression Type: Van Jacobson Compressed TCP/IP 0f 00 IP Address: 192 168 1 1 ##
– PPTP (VPN-0, test) ==> Protocol:CCP(80fd) ConfReq Identifier:0x00 Microsoft PPC 01 00 00 60 ##
– CHAP Login OK (VPN : Remote Dial-in User, Profile index = 1, Name = test, ifno=10)
– PPTP (VPN-0, test) <== Protocol:CCP(80fd) ConfReq Identifier:0x04 Microsoft PPC 01 00 00 00 ##
– PPTP (VPN-0, test) ==> Protocol:CCP(80fd) ConfNak Identifier:0x04 Microsoft PPC 01 00 00 60 ##
– PPTP (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x05 IP Address: 0 0 0 0 Primary Domain Name Server: 0 0 0 0 Primary NetBIOS Name Server: 0 0 0 0 Secondary Domain Name Server: 0 0 0 0 Secondary NetBIOS Name Server: 0 0 0 0 Vendor Specific:…..
– PPTP (VPN-0, test) <== Protocol:IPCP(8021) ConfRej Identifier:0x00 Compression Type: Van Jacobson Compressed TCP/IP 0f 00 ##
– PPTP (VPN-0, test) <== Protocol:CCP(80fd) ConfNak Identifier:0x00 Microsoft PPC 01 00 00 40 ##
– PPTP (VPN-0, test) <== Protocol:CCP(80fd) ConfReq Identifier:0x06 Microsoft PPC 01 00 00 40 ##
– PPTP (VPN-0, test) ==> Protocol:IPCP(8021) ConfRej Identifier:0x05 Primary NetBIOS Name Server: 0 0 0 0 Secondary NetBIOS Name Server: 0 0 0 0 ##
– PPTP (VPN-0, test) ==> Protocol:IPCP(8021) ConfReq Identifier:0x01 IP Address: 192 168 1 1 ##
– PPTP (VPN-0, test) ==> Protocol:CCP(80fd) ConfReq Identifier:0x01 Microsoft PPC 01 00 00 40 ##
– PPTP (VPN-0, test) ==> Protocol:CCP(80fd) ConfAck Identifier:0x06 Microsoft PPC 01 00 00 40 ##
– PPTP (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x07 IP Address: 0 0 0 0 Primary Domain Name Server: 0 0 0 0 Secondary Domain Name Server: 0 0 0 0 ##
– PPTP (VPN-0, test) ==> Protocol:IPCP(8021) ConfNak Identifier:0x07 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ##
– PPTP (VPN-0, test) <== Protocol:IPCP(8021) ConfAck Identifier:0x01 IP Address: 192 168 1 1 ##
– PPTP (VPN-0, test) <== Protocol:CCP(80fd) ConfAck Identifier:0x01 Microsoft PPC 01 00 00 40 ##
– PPTP (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x08 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ##
– ipcp offer requested IP: 192.168.1.10 from client…
– PPTP (VPN-0, test) ==> Protocol:IPCP(8021) ConfAck Identifier:0x08 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ##
– IPCP Opening (VPN : Remote Dial-in User, Profile index = 1, Name = test, ifno=10); Own IP Address : 192.168.1.1 Peer IP Address : 192.168.1.10
– [H2L][UP][PPTP][@1:test]
IPsec
Przykładowe logi z serwera VPN (Vigor2926) dla prawidłowego połączenia:
– IKE <==, Next Payload=ISAKMP_NEXT_SA, Exchange Type = 0x2, Message ID = 0x0
– Responding to Main Mode from 2.2.2.2
– Accept Phase1 proposals : ENCR OAKLEY_AES_CBC, HASH OAKLEY_SHA
– IKE ==>, Next Payload=ISAKMP_NEXT_SA, Exchange Type = 0x2, Message ID = 0x0
– IKE <==, Next Payload=ISAKMP_NEXT_KE, Exchange Type = 0x2, Message ID = 0x0
– NAT-Traversal: Using RFC 3947, no NAT detected
– IKE ==>, Next Payload=ISAKMP_NEXT_KE, Exchange Type = 0x2, Message ID = 0x0
– IKE <==, Next Payload=ISAKMP_NEXT_ID, Exchange Type = 0x2, Message ID = 0x0
– IKE ==>, Next Payload=ISAKMP_NEXT_ID, Exchange Type = 0x2, Message ID = 0x0
– #1 sent MR3, ISAKMP SA established with 2.2.2.2. In/Out Index: 1/0
– IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x1
– Receive client L2L remote network setting is 192.168.1.0/24
– [IPSEC/IKE][Local][1:test][@2.2.2.2] quick_inI1_outR1: match network
– Accept ESP proposal ENCR ESP_AES, HASH AUTH_ALGORITHM_HMAC_SHA1
– Responding to Quick Mode from 2.2.2.2
– IKE ==>, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x1
– IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x1
– [H2l][UP][IPsec][@1:test]
SSL VPN
Przykładowe logi z serwera VPN (Vigor2926) dla prawidłowego połączenia:
– Receive SSL VPN client connect Version: (null); Go SSTPv0
– [SSLTunnel] Dial-in protocol version 0.
– PPP Start ()
– SSLTunnel (VPN-0) ==> Protocol:LCP(c021) ConfReq Identifier:0x00 Authentication Type: CHAP 81 Magic Number: 0x1 ##
– SSLTunnel (VPN-0) <== Protocol:LCP(c021) ConfReq Identifier:0x00 MRU: 1504 Magic Number: 0x3a765a08 ##
– SSLTunnel (VPN-0) ==> Protocol:LCP(c021) ConfAck Identifier:0x00 MRU: 1504 Magic Number: 0x3a765a08 ##
– SSLTunnel (VPN-0) <== Protocol:LCP(c021) ConfAck Identifier:0x00 Authentication Type: CHAP 81 Magic Number: 0x1 ##
– SSLTunnel (VPN-0) ==> Protocol:CHAP(c223) Challenge Identifier:0x01 10 d4 1f c8 2b c4 3f 38 2b 34 1f 28 6b 24 7f 18 6b 44 72 61 79 54 65 6b ##
– SSLTunnel (VPN-0) <== Protocol:CHAP(c223) Response Identifier:0x01 31 1c a8 7e 79 c9 f0 33 12 13 32 5c 60 1a 3a 6d e4 00 00 00 00 00 00 00 00 0b 4b 59 a7 3e 24 bc 12 85 8a 13 22 53 fc ce 92 7e a5 54 06 5e ab 6a 18 00 74 65 73 74 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CHAP(c223) Success Identifier:0x01 S=C680FD7941B270DD5A94A709B848079AF1C61889 M=Welcome to Vigor2926 Series. ##
– SSLTunnel (VPN-0, test) ==> Protocol:IPCP(8021) ConfReq Identifier:0x00 Compression Type: Van Jacobson Compressed TCP/IP 0f 00 IP Address: 192 168 1 1 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfReq Identifier:0x00 Microsoft PPC 01 00 00 60 ##
– CHAP Login OK (VPN : Remote Dial-in User, Profile index = 1, Name = test, ifno=10)
– SSLTunnel (VPN-0, test) <== Protocol:CCP(80fd) ConfReq Identifier:0x01 Microsoft PPC 00 00 00 00 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfNak Identifier:0x01 Microsoft PPC 01 00 00 60 ##
– SSLTunnel (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x02 IP Address: 0 0 0 0 Primary Domain Name Server: 0 0 0 0 Primary NetBIOS Name Server: 0 0 0 0 Secondary Domain Name Server: 0 0 0 0 Secondary NetBIOS Name Server: 0 0 0 0 Vendor Specific:…..
– SSLTunnel (VPN-0, test) <== Protocol:IPCP(8021) ConfRej Identifier:0x00 Compression Type: Van Jacobson Compressed TCP/IP 0f 00 ##
– SSLTunnel (VPN-0, test) <== Protocol:CCP(80fd) ConfNak Identifier:0x00 Microsoft PPC 00 00 00 40 ##
– SSLTunnel (VPN-0, test) <== Protocol:CCP(80fd) ConfReq Identifier:0x03 Microsoft PPC 00 00 00 40 ##
– SSLTunnel (VPN-0, test) ==> Protocol:IPCP(8021) ConfRej Identifier:0x02 Primary NetBIOS Name Server: 0 0 0 0 Secondary NetBIOS Name Server: 0 0 0 0 ##
– SSLTunnel (VPN-0, test) ==> Protocol:IPCP(8021) ConfReq Identifier:0x01 IP Address: 192 168 1 1 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfReq Identifier:0x01 Microsoft PPC 01 00 00 40 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfNak Identifier:0x03 Microsoft PPC 01 00 00 40 ##
– SSLTunnel (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x04 IP Address: 0 0 0 0 Primary Domain Name Server: 0 0 0 0 Secondary Domain Name Server: 0 0 0 0 ##
– SSLTunnel (VPN-0, test) ==> Protocol:IPCP(8021) ConfNak Identifier:0x04 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ##
– SSLTunnel (VPN-0, test) <== Protocol:IPCP(8021) ConfAck Identifier:0x01 IP Address: 192 168 1 1 ##
– SSLTunnel (VPN-0, test) <== Protocol:CCP(80fd) ConfNak Identifier:0x01 Microsoft PPC 00 00 00 40 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfReq Identifier:0x02 Microsoft PPC 01 00 00 40 ##
– SSLTunnel (VPN-0, test) <== Protocol:CCP(80fd) ConfReq Identifier:0x05 Microsoft PPC 00 00 00 40 ##
– SSLTunnel (VPN-0, test) ==> Protocol:CCP(80fd) ConfNak Identifier:0x05 Microsoft PPC 01 00 00 40 ##
– SSLTunnel (VPN-0, test) <== Protocol:IPCP(8021) ConfReq Identifier:0x06 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ## – ipcp offer requested IP: 192.168.1.10 from client…
– SSLTunnel (VPN-0, test) ==> Protocol:IPCP(8021) ConfAck Identifier:0x06 IP Address: 192 168 1 10 Primary Domain Name Server: 8 8 8 8 Secondary Domain Name Server: 8 8 4 4 ##
– IPCP Opening (VPN : Remote Dial-in User, Profile index = 1, Name = test, ifno=10); Own IP Address : 192.168.1.1 Peer IP Address : 192.168.1.10
– [H2L][UP][SSL Tunnel][@1:test]
OpenVPN
Przykładowe logi z serwera VPN (Vigor2926) dla prawidłowego połączenia:
– OpenVPN (VPN-0, 2.2.2.2) PUSH_REPLY,sndbuf 0,rcvbuf 0,socket-flags TCP_NODELAY,route-gateway 192.168.1.1,topology subnet,ifconfig 192.168.1.10 255.255.255.0,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4
– [H2L][UP][OpenVPN][@1:test]